SSH Usernames
I love SSH. It's the most convenient and secure way to manage multiple machines over the internet. It allows me to access my desk machine or my home server from anywhere in the world. It calms my paranoid side with features like SSH Tunneling. In short, SSH is one of my favorite tools.
But the Internet is an interesting place.
Once you expose the famed port 22 to
the outside world, all kinds of users (or rather, robots) want to get in to
"convince" your machine to join their botnets. One common way for these bots is
to hammer your machine with authentication requests using known default
usernames. This is one of the reasons why I usually set the SSH daemon to only
accept whitelisted users and to only allow Public-Key authentication. Another
easy security improvement is to not allow root to log in through SSH. The
lines for these settings in sshd_config look something like this:
PermitRootLogin no # no root login PasswordAuthentication no # only public key auth AllowUsers user1 user2 # user whitelist
These settings usually only let the right users log in to my machines. But the
robots are relentless; they will try regardless. Today I got curious about the
usernames that are being used to try to log in to one of my machines. Of
course, common sense tells us that admin or root are probably among the
most popular ones, but I wanted to look a little closer. The machine in
question uses systemd, so to get the list of usernames I did the following:
$ journalctl -u sshd --no-pager | grep "Invalid user" | awk '{print $8}' > ssh_names.txt
Now I needed a way to visualize my data. Since I wanted only a coarse overview of the distribution of the usernames, I figured that a tag cloud would be enough. A small python script (using word_cloud) later, I could inspect the result:
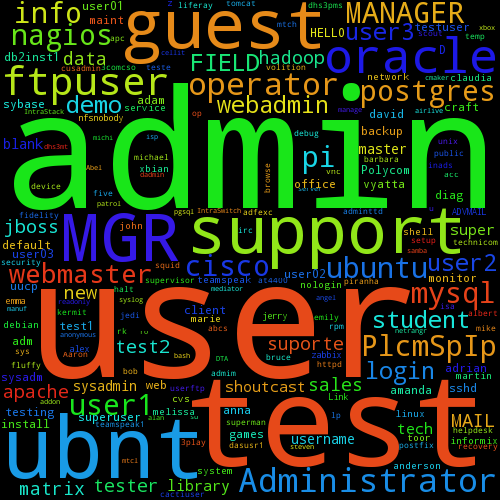
As predicted, admin was quite popular, along with user and test. I
thought the most interesting username was ubnt, which must be the default
admin username of Ubiquiti Networks' AirOS.
The moral of this story: It's probably best to restrict SSH access to a small
set of users; and if your only user is admin with the password password,
then you probably deserve to get hacked.
Dennis